Cheсk Point’s research team once got a message from a Bloomberg journalist named Martyn Williams, who had been forwarded a copy of a North Korean antivirus by someone allegedly from Japan. One does not encounter North Korean software often, so experts Mark Lechtik and Michael Kajiloti were only too glad to see what the antivirus tool was like. They presented the results of their study at the hackers’ congress 35C3.
But before we discuss the North Korean antivirus product, we should probably briefly cover the relationship North Korea has with the Internet and vice versa.
North Korea’s role in developing the global network
Attribution — crafting a justified claim that a specific group from a specific country attempted a specific attack — is an altogether hit-and-miss business. Interpreting evidence is difficult, following the wrong lead is easy, and so forth. Yet at some point, several research groups were jointly attributing some attacks to North Korea. It is also widely believed that North Korea uses state-supported groups of hackers, whose business is to earn money for the regime. Of course, DPRK officials deny this.
That said, the Internet as such is virtually nonexistent in North Korea: the World Wide Web can be accessed only by a chosen few, whereas the bulk of the population is restricted to the domestic intranet, which is called Kwangmyong: a network purged of all information from “the decaying West.” The West, in turn, also has little opportunity to peep into the North Korean network, so every bit of information on the subject is a treat.
Korean–Japanese antivirus
The first logical question is: Why would North Korea, lacking the Internet, want an antivirus? First, for protection against viruses smuggled into the country on memory sticks containing Western articles, South Korean TV series, and other information not officially available in the DPRK. Contraband memory sticks are surprisingly widespread in these parts. Second, and less obvious, it looks like North Korea was going to market this antivirus internationally — at least one of its versions includes an English interface.
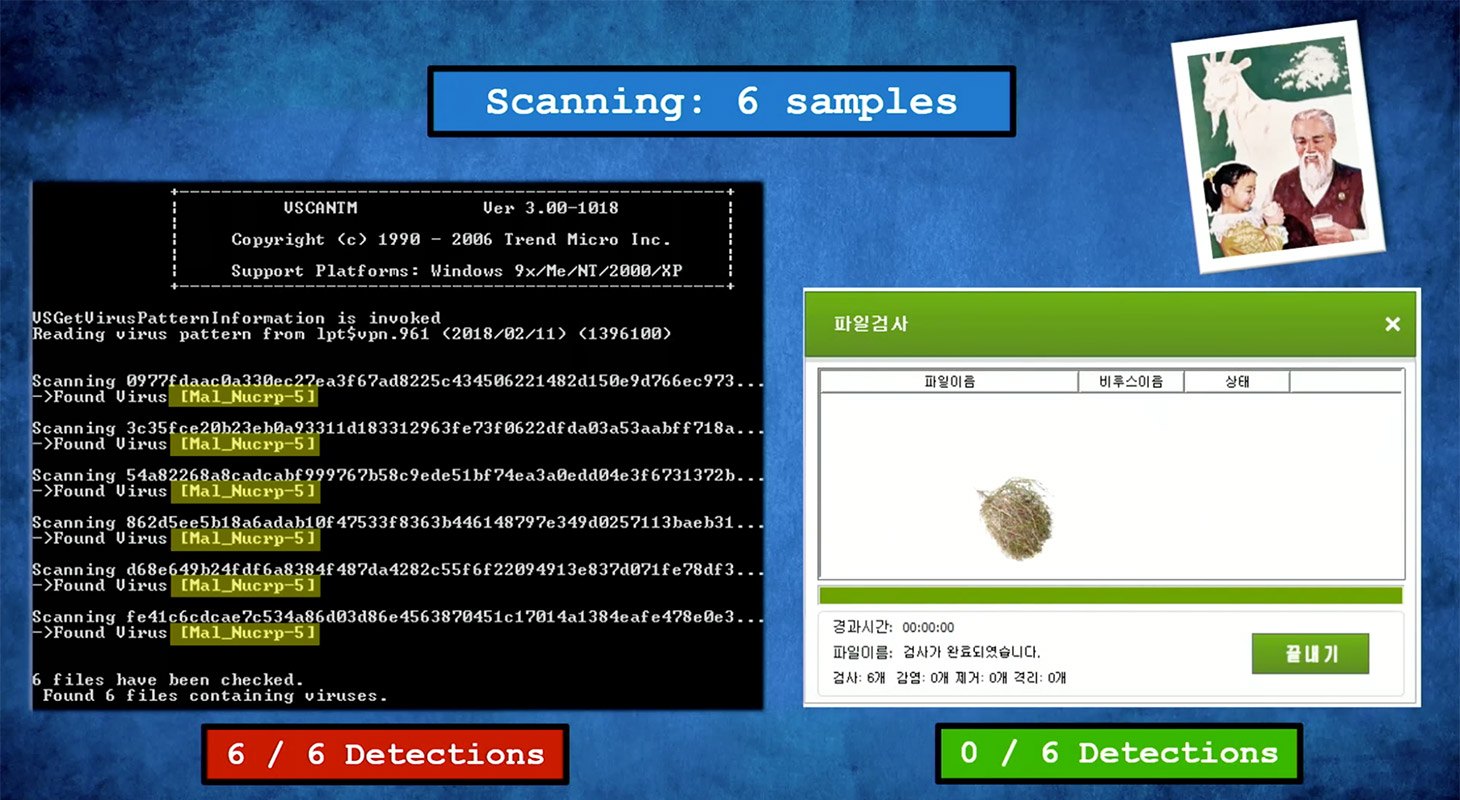
The second question, no less logical, is: Where would the DPRK get antivirus software of its own? A sophisticated product like that is rather difficult to create from the ground up, especially given limited resources. The experts from Check Point addressed this question, too, only to draw an interesting conclusion: The 2013 version of the Korean antivirus (which was what they had available) was using the engine of a popular antivirus solution by Trend Micro, although from 2008.
The Korean developers were clearly unwilling to let anyone meddle with the product’s code; many of its components were protected with Themida — a wrapper program designed to obstruct reverse engineering. Yet those who were packing up the SiliVaccine components had neglected to use much of the impressive Themida toolkit, so the Check Point team was able to access the program code.
About one-quarter of the SiliVaccine code fully matches the elements of the Trend Micro antivirus code, but certain functions were slightly modified. The research team approached Trend Micro with a question: Where would North Korea get the source code of a Japanese-made antivirus product? Trend Micro said they didn’t know how the DPRK had gotten hold of the engine, so they believed it was used illegally. They also mentioned that the engine could have been used by Trend Micro’s partners, who were marketing protection solutions under brand names of their own. At least this gives a clue how the source code could have landed in the hands of North Korean programmers.
The North Koreans were clearly trying to conceal the fact that SiliVaccine was based on Trend Micro’s engine, so they added some bells and whistles. Thus, at first sight it might seem that these two antiviruses were using totally different processes for virus signatures: Trend Micro uses just one signature file, whereas SiliVaccine has 20. However, as soon as the engine boots up, all of these files are merged into one. As to the signatures themselves, they suspiciously resemble those used by Trend Micro: For example, if Trend Micro uses a signature TROJ_STEAL-1 for certain malware, SiliVaccine will have Trj.Steal.B. They just change letter case, replace dashes and underscores with full stops, and add a few more minor changes.
In the course of their investigation into the North Korean antivirus, the research team reported lots of bugs and oddities. For example, the program features a component supposedly intended to scan a file for viruses, should the user right-click on it in File Explorer and select the appropriate option from the menu. The menu does feature that option, but clicking on it gets you nowhere.
One more oddity: The antivirus comes with a driver that collects information about network connections and … does nothing with it. In theory, the driver should be accessed by some other files, but no other SiliVaccine files ever use it.
Some components were encrypted with BopCrypt — a packaging tool popular in the Russian-speaking Internet community some 15 years ago. Some components appeared to consist mostly of junk code. The impression was that the main function of some of the files was to just waste time, doing nothing. Furthermore, the researchers developed an opinion that the authors of at least some SiliVaccine components had tried their hand at reverse engineering but failed to figure out exactly how the code worked.
Also, it looked like the people who wrote different parts of the code were not very good at teamwork. For example, one file is supposed to trigger a function of another with a parameter that is set to a certain value, whereas the second file is specifically programmed to do nothing if that value comes on.
All considered, the North Korean SiliVaccine turned out to be a much reworked and very buggy version of Trend Micro’s antivirus.
Could it be malware?
Anyone familiar with the DPRK’s external Internet policy has to ask: What if it’s actually a Trojan? What if this product was made to implant malware or something of the sort? Check Point answers that, too.
Their findings were, again, interesting. To begin with, the SiliVaccine antivirus itself appears to be clean. It was not found to contain any malware features. And yet, the EXE files mention one signature the engine is to ignore. If a scanned file should be infected with malware of that signature, SiliVaccine will simply let it live.
Sure enough, the researchers were curious about exactly which piece of malware it was, so they attempted to cross-check this signature from the SiliVaccine virus base against the corresponding one from the Trend Micro base. But it turned out to be a heuristic signature, one given to all files demonstrating a specific behavior, so they were unable to figure out exactly which malware file the North Korean antivirus was programmed to ignore. But they found that SiliVaccine developers had at one point made a misprint and added to their allowlist a nonvalid signature.
Although the SiliVaccine installer itself wasn’t malicious, the archive received by the Bloomberg journalist from an unknown engineer allegedly from Japan also contained another file. Its name suggested that it was a patch for SiliVaccine, whereas its metadata claimed it was related to Microsoft’s automatic updates.
The Check Point researchers analyzed this file to discover it was a piece of malware called Jaku, first described by Forcepoint in 2016. According to the explanations provided by Forcepoint in its study, Jaku was used against individuals linked, one way or another, with North Korea, and it was also clearly connected with DarkHotel — a Korean-speaking group whose activities were covered in a study we published in 2014.
Martyn Williams — the Bloomberg journalist who received the letter containing SiliVaccine — writes a lot about North Korea, so researchers assumed the whole scheme involving mail with the antivirus in an attachment could have been a targeted attack against him; his work is hardly appreciated by the DPRK leaders. As for the SiliVaccine, it appears to be a real antivirus product, quite likely used in North Korea — for lack of better options.
 35c3
35c3




 Tips
Tips