Problems with unwanted mail
It is difficult to find an email user who has never received any kind of spam. Some get mail from dubious correspondents in their inboxes from time to time, and others have to purge hundreds of those messages every day. Mass mailing is a serious problem not just because it consumes time and physical resources for the process of sorting emails, but also because they are a frequent source of malicious content. One infamous example of cyberweapons – Duqu Trojan – infects systems after an apparently harmless text document has been opened, thereby exploiting a vulnerable system. Moreover, attackers actively use the so-called spearphishing method (targeted mailing with a fake sender’s address to a specific list of email addresses) to penetrate the targeted organization’s infrastructure. This sort of an attack was implemented in the APT “Hellsing“, when cybercriminals delivered malware via targeted emails with attachments.
#Antispam technologies: secure mail for people and business
Tweet
It’s no wonder attackers use spam as a means of distributing malware, which is attached to the message body. Spam messages may contain links to malicious web resources, which are the starting points for phishing or contain malicious code. After making it to the “Inbox” the letter may become an entry way for a spying Trojan that steals valuable data or an encrypting ransomware which demands money for decoding necessary files. In the case of a Trojan encryptor getting into a workstation, it is not just personal user files that are exposed, but also the working data, and eventually the business process is damaged.
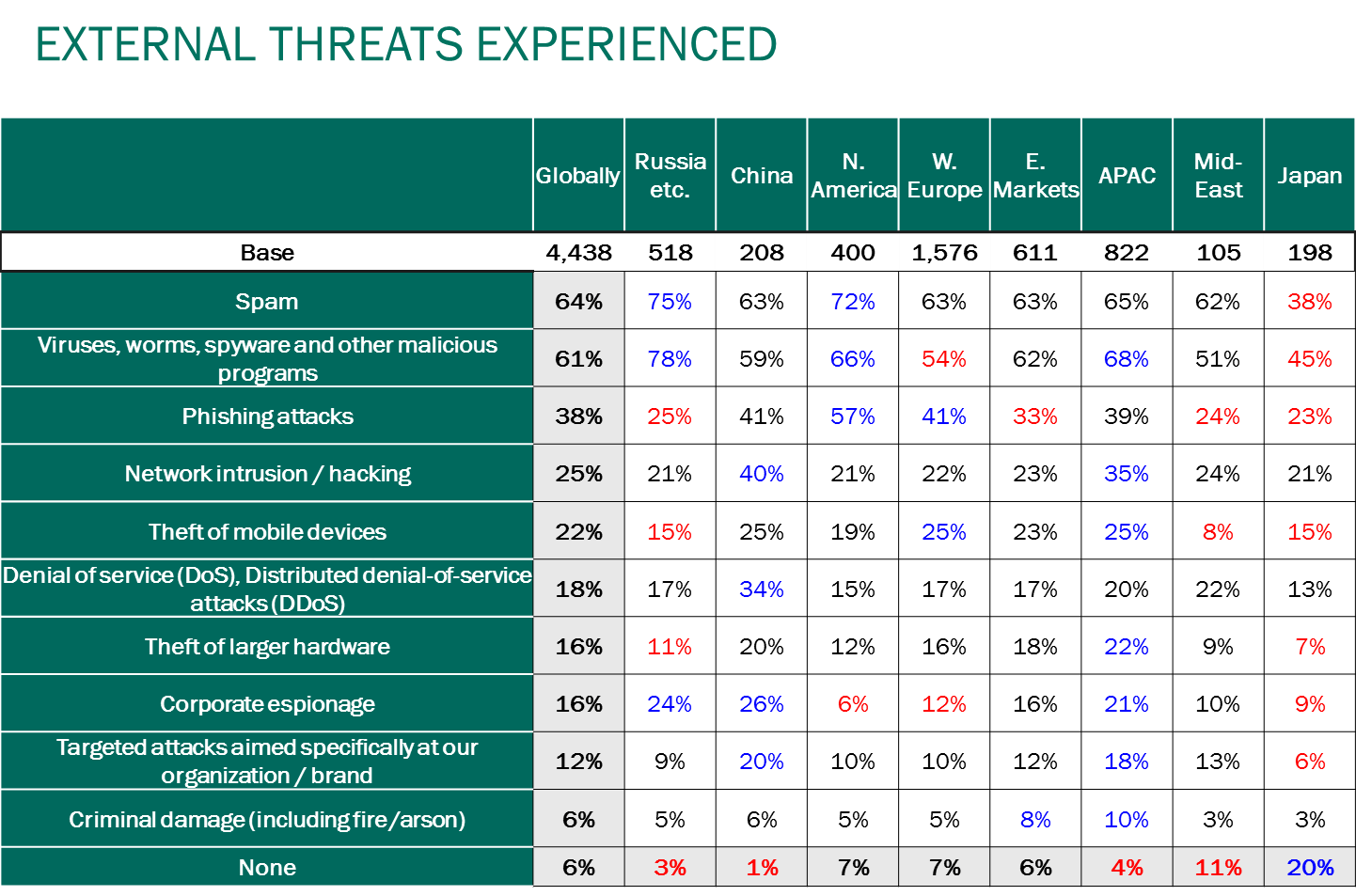
According to a B2B International 2014 Survey, spam has become the primary threat among other external threats to the corporate sector. 64% of all respondents defined spam as most dangerous to their IT-infrastructure.
Attackers improve social engineering techniques, which are then used in the preparation of the malicious message. For example, Kaspersky Lab’s experts detect an increase of messages containing malicious attachments disguised as various financial documents: notifications of fines, remittances, unpaid bills, payments, orders and complaints, e-tickets, etc. Among these fraudulent notifications there are also fake messages on behalf of public services, shopping malls, booking services, airlines and other well known organizations. These deceiving techniques urge users to read the message and open malicious attachments or follow a malicious link in the message body.
Furthermore, Kaspersky Lab’s experts found that the proportion of spam in March 2015 amounted to 56.17% of the total email traffic. At the same time, the monthly share of spam in email traffic shows that malicious activity waxes on holidays and vacations. Given these facts and the ingenuity of fraudsters, one must implement available technologies to effectively counter this threat.

The percentage of spam in email traffic (October 2014 – March 2015)
Email is still of great importance for corporate infrastructure communication. However, one should understand that cloud email clients have generated an additional source of troubles for IT-infrastructure, because now an employee has access not just to the corporate mail, but to his or her personal correspondence, too, which also needs to be protected against spam. Therefore, fighting unwanted and often dangerous correspondence is a must for comprehensive protection of infrastructure and requires solutions which are based on effective antispam technologies.
The proportion of #spam in March 2015 amounted to 56.17% of the total email traffic.
Tweet
The methods of keeping your “Inbox” tidy
- To successfully counter the ceaseless stream of junk mail we suggest you follow a few simple rules:
- Create two email accounts – one public and another corporate. Use the latter address exclusively for business correspondence with familiar people. Under no circumstances open attachments until you are sure of their safety.
- Do not reuse the same password for both email accounts – it will help avoid trouble if cybercriminals with access to your personal correspondence are able to compromise your corporate email, and vice versa.
- Never publish your corporate email on the Internet or use it to register on web resources – the second public address is good enough for that.
- In the case of spam or messages from unknown persons in your Inbox, do not open attachments or follow links. Don’t bother to respond to such letters either.
- Enable security solutions providing advanced technology to combat spam.
 antispam
antispam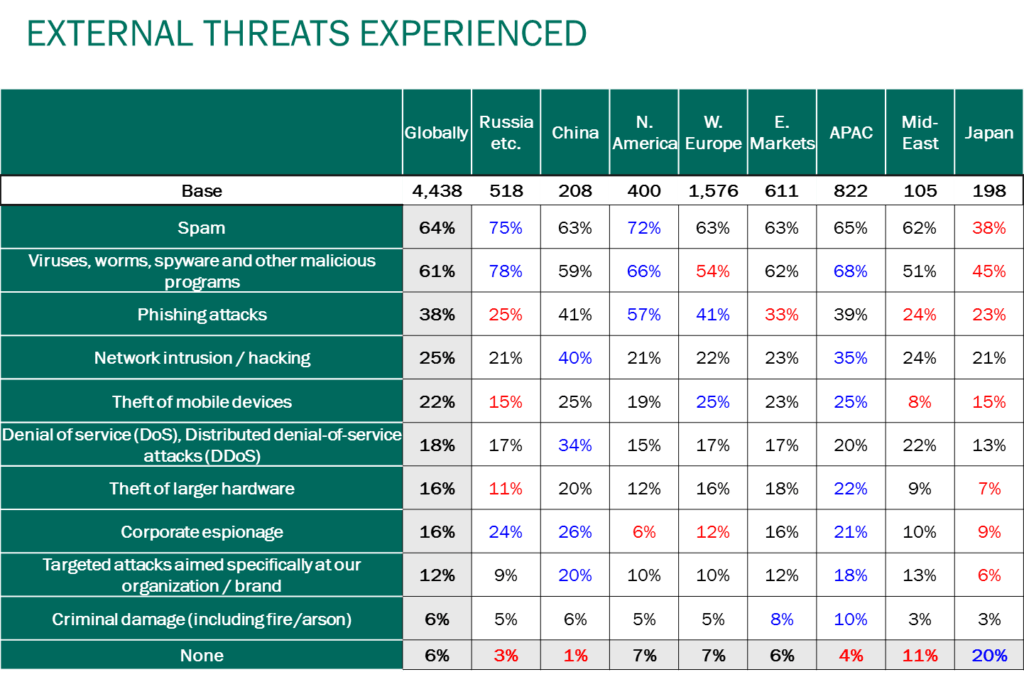

 Tips
Tips