Four of the 10 most pressing problems facing businesses are linked to information security, and cyber-threats, the most significant of those four, came a close second in the overall top 10 just behind fears of economic instability. These were some of the key findings of a survey carried out by B2B International in July 2012.
The fact that cyber-threats are seen as such a major risk probably has something to do with the constantly growing number of malicious programs and ever-increasing activity of cybercriminals. In 2011 Kaspersky Lab detected an average of 70,000 new malicious objects a day, but in 2012 that figure has already grown to 125,000. On average, the company’s products block over 350 million malware attacks and 30 million malicious links every quarter. This should be enough to convince companies that measures need to be taken to protect IT infrastructure, but many remain reluctant to make the necessary changes. According to the survey, 41% of companies lack sufficient IT protection to withstand a cyber-attack.
Intellectual property theft, fraud and industrial espionage were among the other information security-related issues mentioned by those who took part in the survey. These threats existed long before the advent of computers, but cyber-attacks have now become the preferred method for carrying out these activities. Readiness to face these threats also leaves much to be desired: in approximately half of all cases, corporate infrastructure is no match for espionage or intellectual property theft.
Another major problem is one which is going to become increasingly relevant in the near future – targeted attacks on an organization’s infrastructure intended to steal critical information. Such attacks involve sending messages containing malicious links or attachments to a company’s internal email addresses, exploiting previously unknown vulnerabilities in popular software, using websites with infected pages and other tricks. Unlike ordinary cyber-threats that are designed to cover as many computers as possible, targeted attacks are better organized and are aimed at specific companies. Moreover, the techniques used by cybercriminals may change, with the attacks themselves continuing until the desired result is achieved, i.e. until the system is penetrated.
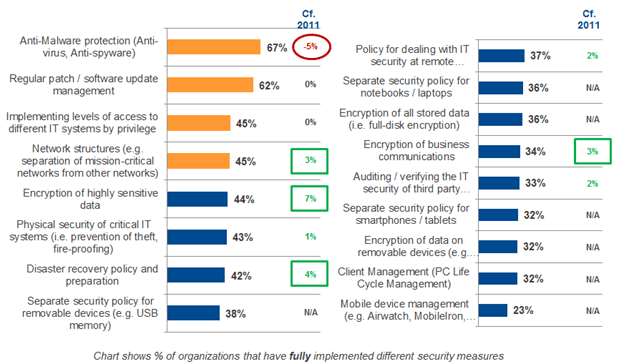
There are several obvious and effective measures that companies can take to combat cyber-threats. The main protection methods include installing antivirus solutions on elements of the infrastructure and regularly updating programs and the OS in order to eliminate possible vulnerabilities that could be exploited by attackers to infect a computer. Organizational measures can also be taken, including isolating critical elements of the IT infrastructure and dividing employees into groups with different information access levels. As regards actions affecting employees, the priorities in this area are shifted towards improving productivity: companies most commonly restrict access to social networks and online games.
 statistics
statistics
 Tips
Tips