The “Jeep hackers,” Charlie Miller and Chris Valasek, got their nickname and achieved fame last year when they remotely hijacked a moving Jeep Cherokee. It’s a year later now, and the duo has found more dangerous vulnerabilities. Miller and Valasek shared their findings at Black Hat USA 2016, and today we are spreading the word further.
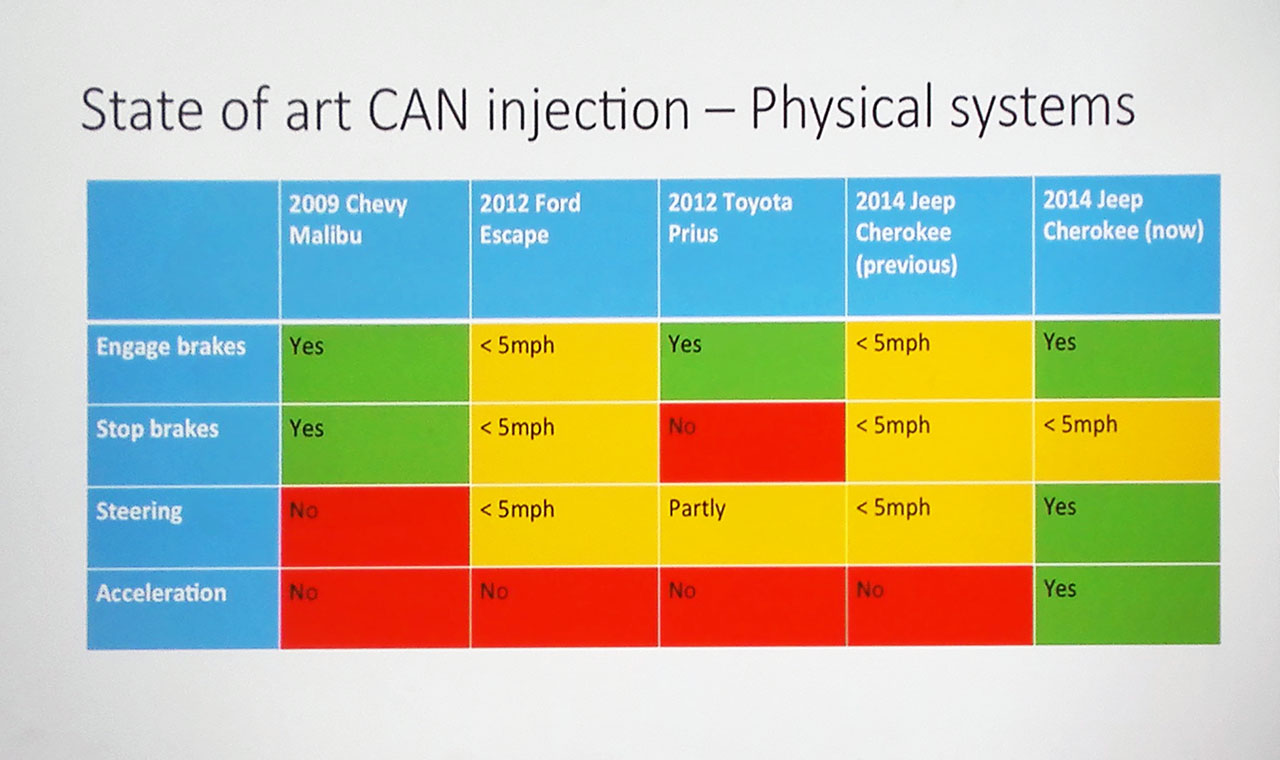
During the past year, research experts were able to perform some of the most dangerous actions (turning the steering wheel, braking, and accelerating), but only at very low speeds — up to 5 miles per hour. The hack took advantage of vulnerabilities in cars’ smart features, such as automated parking assistance, and the Jeep’s diagnostic mode.
#BlackHat 2015: The full story of how that Jeep was hacked https://t.co/y0d6k8UE4n #bhUSA pic.twitter.com/SWulPz4Et7
— Kaspersky Lab (@kaspersky) August 7, 2015
These features are typically used at low speed or with the engine off. If you try to exploit them at high speed, the system will register a conflict and the smart feature won’t be activated — unless you bypass that limitation. And that’s exactly what the “Jeep hackers” have achieved this year.
The onboard computer receives speedometer and tachometer readings from messages sent through the CAN bus, which is sort of like a vehicle’s local network. If you want to bypass security restrictions, you have to fake the messages and make the car believe that it is standing still while it’s actually tearing down the highway.
Miller and Valasek did it — they infected one of onboard electronic units with the help of a malicious patch. As the result, they were able to use the CAN bus to send fake readings. The method is quite simple. Messages with readings are usually numbered. When an electronic unit receives two messages with the same number, it trusts the first one and rejects the second.
So if hackers assign the right numbers to fake messages and send them before the system sends real messages, the system trusts the fake data and discards the real.
Once researchers solved this problem, they learned to pull off even more dangerous, unprecedented tricks than last year — and at any speed. For example, they could take control of the steering booster and command it to turn the wheel. Or engage the parking brake, no matter how hard the driver tries to stop them — the control in the car becomes useless during the attack. They also learned to alter cruise control settings to quickly accelerate.
But don’t think that hackers took full control over the car — that’s not exactly how it went down. They could not, for example route the car wherever they wanted. And during an attack, the driver can hit the brake pedal to stop the car or try to overcome the power steering (if they are strong and attentive enough). Researchers stressed that drivers needed to be focused on the car’s movement and the road to realize in time that something was going wrong.
We need to add that if such attacks come unexpectedly, they will be even more dangerous. Hackers can raise their chance of success by distracting drivers with environmental changes — suddenly turning on loud music or blasting the air conditioning, for example — tricks Miller and Valasek have already pulled off. While the driver focuses on dealing with the “buggy electronics,” hackers can suddenly turn the wheel, accelerate, or activate the parking brake.
We have good news as well. First, for Fiat Chrysler, developer of the hacked cars: At the end of their report at Black Hat USA 2016, security experts said they would stop hacking the long-suffering Jeep.
Second, for owners of Fiat Chrysler cars: The company didn’t ignore the researchers’ findings. It patched a number of the vulnerabilities Miller and Valasek discovered. For example, the Sprint cellular network, which the cars use to connect to the Internet, now blocks TCP traffic — that means last year’s remote hack doesn’t work anymore.
Finally, Fiat Chrysler recently launched a bug bounty program, compensating people who find and report bugs and vulnerabilities. Tesla and General Motors have similar programs. Though Fiat Chrysler’s program is not the best of its kind, and the bounties are rather small by cybersecurity standards, it’s nonetheless a step in the right direction.
 blackhat16
blackhat16



 Tips
Tips