Distributed denial-of-service attacks have been plaguing various entities across the world for years, and their intensity grows constantly as the attackers employ novel techniques of amplification. Novel approaches aren’t limited to boosting the attacks’ power, however. Kaspersky Lab has just released its Q2 report on DDoS activities on the Web, showing that this part of the global threat landscape is extremely volatile and permanently evolving.
Main trends
In the second quarter of 2015 Kaspersky Lab’s researchers identified three main trends in which these threats evolve.
- Invent and use new techniques aimed at launching more powerful attacks without increasing botnet sizes;
- Create botnets of devices connected to the Internet, and use them to carry out DDoS attacks;
- Develop DDoS modules for malware toolkits with which to carry out targeted attacks.
The detailed research is available at Securelist. We, in turn, would rather focus on just two highlights – device botnets and DDoS modules in malware toolkits.
Routers avalanching
A whole botnet made of home and small-business routers was detected by security researchers earlier this year – it was actually used to launch a potent DDoS attack.
Routers, especially those sold to households and smaller businesses, are among the most overlooked pieces of equipment, despite their importance. They are usually set up once, and unless it is absolutely necessary, no further attention is given.
At the same time, as practice shows, a considerable number of vulnerabilities and configuration shortcomings in their firmware exist, and even if manufacturers release updates, those aren’t necessarily patched quickly.
Which creates a great opportunity for criminals to abuse these pieces of equipment successfully.
The botnet consisting entirely of routers is something new, although it is not the first time that routers are under attack, and it is not actually the first time that non-PC computerized devices became part of a botnet. The spamming fridge still feels like a curio of sorts, but unless the manufacturers of internet-enabled household equipment implement a security-by-design approach, occurrences like that will be encountered more and more often.
And it’s doubtful that businesses would want spying coffee-machines in their meeting rooms.
But we were talking about DDoS…
Indeed. There is no DDoS without an attack platform, which usually consists of a (sheer) number of devices under attackers’ control – and these devices won’t just fall under the criminals’ control if they are protected.
In most cases (and in this particular one), the root of the problem is that the device owners keep factory login:password pairs, which makes the equipment an easy prey.
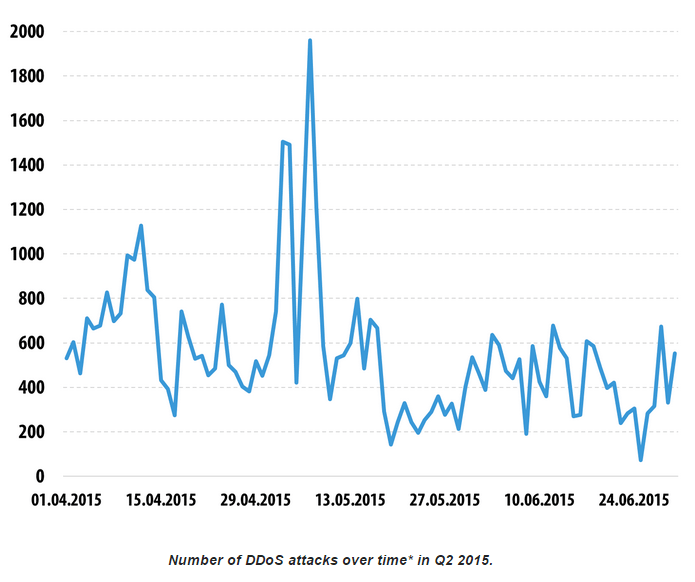
For some reason DDoS attacks spiked in early May (image taken from Securelist.com).And what is so important with DDoS modules?
DDoS functionality added to malware that essentially have another primary purpose has happened before.
This time, however, a DDoS module had been discovered in a largely unexpected place: in a toolkit used by an APT group dubbed Animal Farm. They have added Nbot Trojan, designed to arrange a botnet and carry out DDoS attacks. NBot maintains a large number of distributed attack scenarios – this is evidence that the botnet had been arranged by the cybercriminals to launch large-scale DDoS attacks. This was most likely done in order to hang smokescreens or create a diversion of sorts to cover their other activities.
NBot is just one of the Trojans in the toolkit of Animal Farm. It’s unclear whether it was actually used to launch a DDoS attack by the Animal Farm operators, but for all we know, they can.
An armored umbrella against the trouble
It was reported earlier this year that less than 40% of the companies took any consistent efforts to protect themselves from DDoS attacks. For some time it was deemed impossible or overly expensive to have such protection, while the startling data on DDoS attacks peaking at 100-400 Gbps could give the impression that there was little that could be done against such avalanches of junk data.
But, in fact, protection is available – in the form of Kaspersky DDoS Protection, the total defence and mitigation solution designed to protect businesses from the damage DDoS attacks may incur. Kaspersky DDoS Protection combines Kaspersky Lab’s proven expertise with in-house technology such as DDoS Intelligence. It is a system that analyzes the information sent from C&C servers to botnets, and aims to improve protection against DDoS attacks.
For more information on how Kaspersky DDoS Protection work please visit here.
A detailed report on DDoS attacks in Q2, 2015 is available at Securelist.
For more information on DDoS attacks and how they affect businesses please visit here.
 ddos
ddos