In last week’s post we mentioned that at a certain moment in history, the cybersecurity field expanded beyond “simple” antivirus solutions. Those solutions aren’t exactly simple, but there are many other threats “an antivirus” can’t address.
When did it all begin?
The Internet is arguably the greatest achievement of mankind since harnessing nuclear power led to the formation of what is now known as the threat landscape.
Many of us, at least people older than 25, may remember those fabulous global virus epidemics – ILoveYou/LoveLetter, Anna Kournikova, Code Red, Melissa – all of them happening in the late 1990s and early 2000s. Then there was the SQL Slammer worm, resulting in a global Internet slowdown (2003) and MyDoom worm (2004) that possibly still holds the crown for the fastest-spreading mass mailer worm.
What made them possible is the broadband access to the Internet. Once a quick software delivery became a reality, attackers couldn’t help but abuse it for their malicious “needs.” Initially, the internet “worms” were acts of vandalism rather than criminal offenses, but as soon as stealing data functionality was introduced to malware (such as a worm taking addresses from a mail client address book and sending copies of itself to them), Pandora’s box was opened.
More than an #antivirus, p.2: When and why the antivirus alone became insufficient
Tweet
There is a decent timeline of malware on Wikipedia, covering (conceivably) all of the “groundbreaking” computer viruses ever created. It’s clear that the first half of the 2000s is when the worms became a primary threat, but everything started changing in the second half of the decade.
At that time, cybercrime began morphing into something much different than just vandalistic acts. In 2007, Storm Worm and Zeus Trojan emerged, both created with an intent to “gather” the PCs into a botnet. Then Rustock.C, a spambot-type malware with advanced rootkit capabilities, detected on Microsoft systems.
Add here the ever-growing number of new malware, a phishing threat, that was a”fully industrialized part of the economy of crime” by the mid-2000s, and many other “internet-borne” threats made possible by ubiquitous broadband connection – and the fact that crooks recognized how profitable cybercrime can be.
So there is yet another timeline
Take a look.
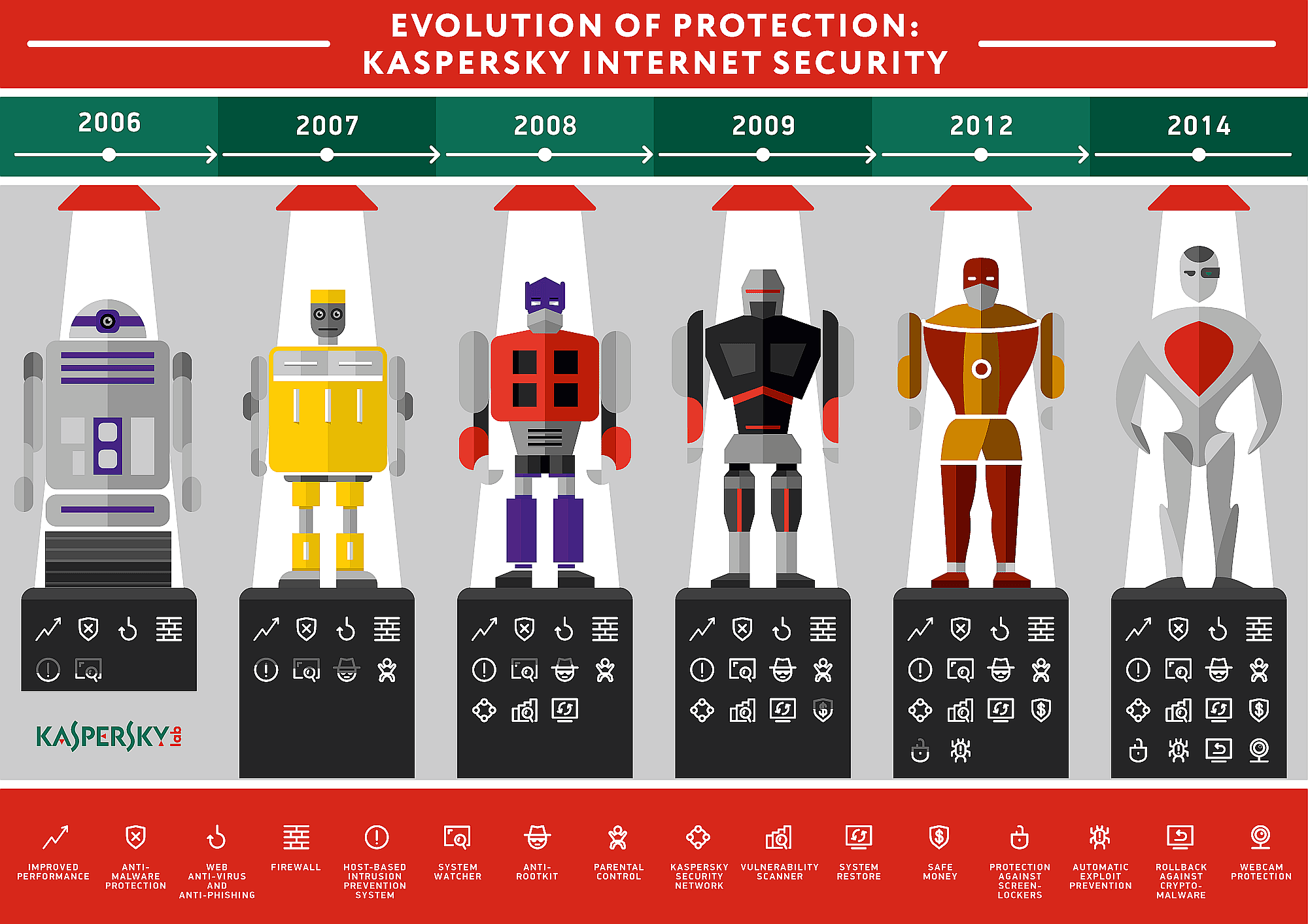
That’s a diagram of add functionality to Kaspersky Lab’s security products, namely Kaspersky Internet Security. It is a customer-level suite, not a business-grade one, but all of the security solutions Kaspersky Lab offers share the same codebase, so the essential protection is the same.
This “diagram of evolution” is rather indicative: The new protective functions were added in response to emerging threats. By 2006, there was firewall, web antivirus and anti-phishing, along with a host-based intrusion prevention system against network attacks – something that an “antivirus” could not handle.
In 2008, anti-rootkit and parental control were added, and Kaspersky Security Network launched. By 2012, Automatic Exploit Prevention system was integrated, and by 2014, a rollback against crypto-malware – in response to exploits and encrypting ransomware becoming all too common threats, for both end-users and businesses.
By that time, the question whether antivirus is alive or dead had become quite common, and much discussed. Still, the malware protection modules are not going away, it is still in the core, but many other things have accreted along. It’s just not feasible to call a security solution, either for individual users or for businesses, “an antivirus.” There’s more than that.
In one of the future posts we’ll talk about business-specific threats and the tools for battling them. Stay tuned!
 Antivirus
Antivirus

 Tips
Tips