(Updated on Tuesday, May 16)
A few days ago saw the beginning of the Trojan encryptor WannaCry outbreak. It appears to be pandemic — a global epidemic. We counted more than 45,000 cases of the attack in just one day, but the true number is much higher.
What happened?
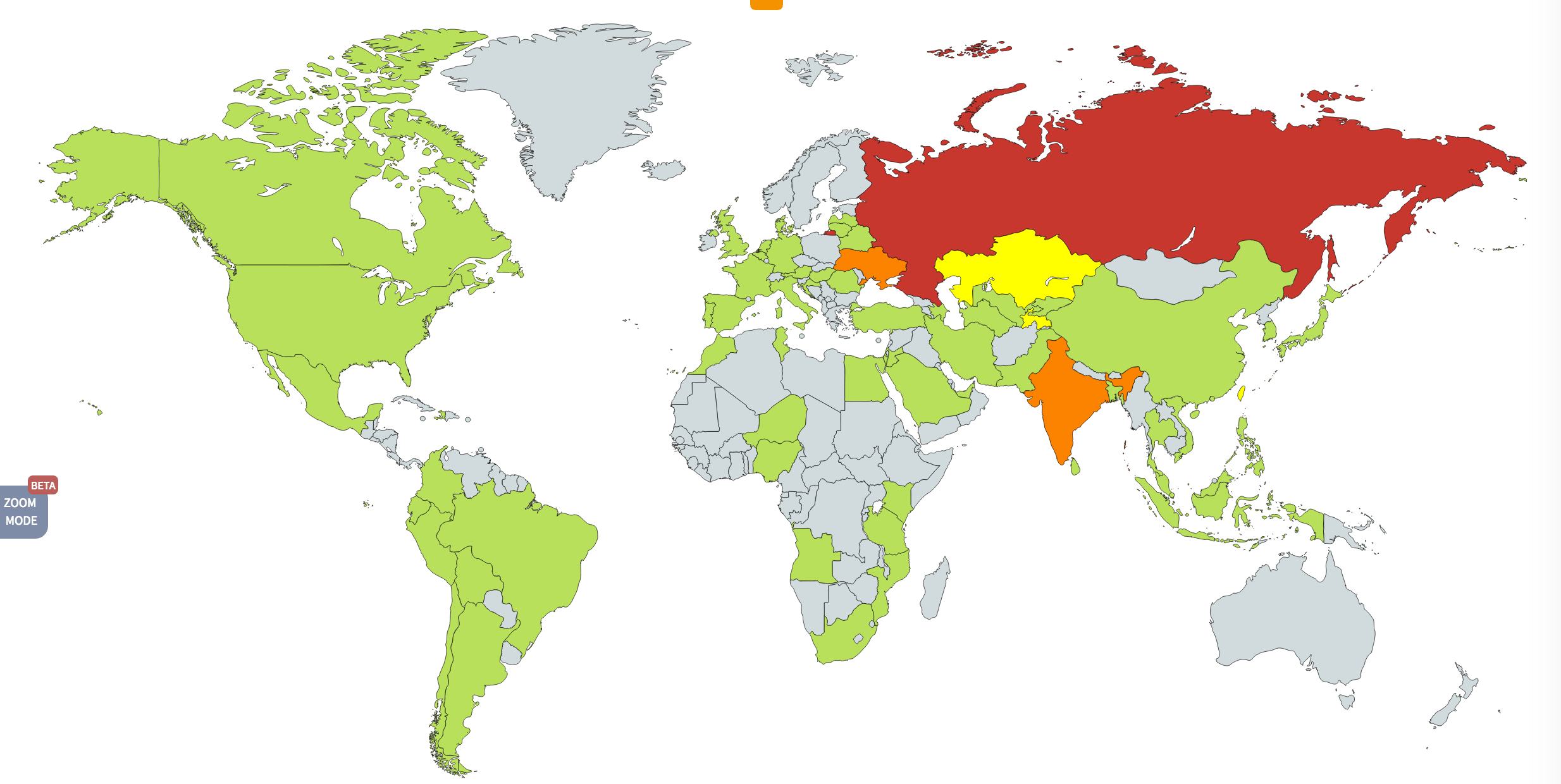
Several large organizations reported an infection simultaneously. Among them were several British hospitals that had to suspend their operations. According to data released by third parties, WannaCry has infected more than 200,000 computers. The sheer number of infections is a big part of the reason it has drawn so much attention.
The largest number of attacks occurred in Russia, but Ukraine, India, and Taiwan have suffered much damage from WannaCry as well. In just the first day of the attack, we found WannaCry in 74 countries.
What is WannaCry?
Generally, WannaCry comes in two parts. First, it’s an exploit whose purposes are infection and propagation. The second part is an encryptor that is downloaded to a computer after it has been infected.
The first part is the main difference between WannaCry and the majority of encryptors. To infect a computer with a common encryptor, a user has to make a mistake, for example by clicking a suspicious link, allowing Word to run a malicious macro, or downloading a suspicious attachment from an e-mail message. A system can be infected with WannaCry without the user doing anything.
WannaCry: Exploit and propagation
The creators of WannaCry have taken advantage of the Windows exploit known as EternalBlue, which relies on a vulnerability that Microsoft patched in security update MS17-010, dated March 14 of this year. By using the exploit, the malefactors could gain remote access to computers and install the encryptor.
How to properly update #Windows to protect your computer from #WannaCry https://t.co/QevgKiqEz0 #ransomware pic.twitter.com/7AKhc2YLFv
— Kaspersky (@kaspersky) May 17, 2017
If you have the update installed, then this vulnerability no longer exists for you, and attempts to hack the computer remotely through the vulnerability will fail. However, researchers from Kaspersky Lab’s GReAT (Global Research & Analysis Team) would like to emphasize that patching the vulnerability will not deter the encryptor entirely. Therefore, if you launch it somehow (see the above on making a mistake), then that patch will do you no good.
After hacking a computer successfully, WannaCry attempts to spread itself over the local network onto other computers, in the manner of a computer worm. The encryptor scans other computers for the same vulnerability that can be exploited with the help of EternalBlue, and when WannaCry finds a vulnerable machine, it attacks the machine and encrypts files on it.
Therefore, by infecting one computer, WannaCry can infect an entire local area network and encrypt all of the computers on the network. That’s why large companies suffered the most from the WannaCry attack — the more computers on the network, the greater the damage.
WannaCry: Encryptor
As an encryptor, WannaCry (sometimes called WCrypt or, for no discernable reason, WannaCry Decryptor) behaves like any other encryptor; it encrypts files on a computer and demands ransom to decrypt them. It most closely resembles a variation of the infamous CryptXXX Trojan.
WannaCry encrypts files of various types (the full list is here) including office documents, pictures, videos, archives, and other file formats that potentially contain critical user data. The extensions of the encrypted files are renamed .WCRY, and the files become completely inaccessible.
After this, the Trojan changes the desktop wallpaper to a picture that contains information about the infection and actions that the user supposedly has to perform to recover the files. WannaCry spreads notifications as text files with the same information across folders on the computer to ensure that the user receives the message.
As usual, the actions entail transferring a certain amount of money, in bitcoins, to the wallet of the perpetrators. After that, they say, they will decrypt all of the files. Initially, cybercriminals demanded $300 but then raised the stakes to $600.
In this case, the malefactors also try to intimidate victims by stating that the ransom amount will be increased in three days — and, moreover, that after seven days the files will be impossible to decrypt.
As ever, we do not recommend paying the ransom. Perhaps the most compelling reason not to give in is that there’s no guarantee that the criminals will decrypt your files after receiving the ransom. As a matter of fact, researchers have shown that other cyberextortionists sometimes simply delete user data.
How a domain registration suspended infection — but why it is probably not over yet
Interestingly enough, a researcher going by name Malwaretech managed to suspend infection by registering a domain with a long and nonsensical name.
It turned out that some versions of WannaCry addressed that very domain, and if they did not receive a positive reply, then they would install the encryptor and start their dirty work. If there was a reply (that is, if the domain had been registered), then the malware would stop all of its activities.
After finding the reference to this domain in the Trojan’s code, the researcher registered the domain, thus suspending the attack. In the remainder of the day, the domain was addressed tens of thousands of times, which means that tens of thousands of computers were spared.
There is a theory that this functionality was built into WannaCry — like a circuit breaker — in case something went wrong. Another theory, embraced by the researcher himself, is that it is a way to complicate the analysis of the malware’s behavior. Testing environments used in research are often designed such that any domain returns a positive response; in such cases, the Trojan would do nothing in the testing environment.
Regrettably, for new versions of the Trojan, all the criminals have to do is change the domain name indicated as the “circuit breaker” and infections will resume. Therefore, it is very likely that the WannaCry outbreak will continue.
How to defend against WannaCry
Unfortunately, there is currently no way to decrypt files that have been encrypted by WannaCry (however, our researchers are on it). For now, prevention is the only hope.
Here are several pieces of advice on how to prevent infection and minimize damage.
- If you already have a Kaspersky Lab security solution installed on your system, then we recommend doing the following: Manually run a scan for critical areas, and if the solution detects MEM:Trojan.Win64.EquationDrug.gen (that is how our antivirus solutions detect WannaCry), remove it and reboot your system.
- If you’re a Kaspersky security user, keep System Watcher on. It’s essential to fight any new variants of the malware that might emerge.
- Install software updates. This case desperately calls for all Windows users to install the MS17-010 system security update. Microsoft even released it for systems that are no longer officially supported, such as Windows XP or Windows 2003. Seriously, install it right now; it’s very important.
- Create file backups on a regular basis and store the copies on storage devices that are not constantly connected to the computer. If you have a recent backup copy, then an encryptor infection is not a catastrophe; you can spend a few hours reinstalling the operating system and apps, then restore your files and move on. If you’re just too busy to handle a backup, take advantage of the backup feature built into Kaspersky Total Security, which can automate the process.
- Use a reliable antivirus. Kaspersky Internet Security can detect WannaCry both locally and during attempts to spread it over a network. Moreover, System Watcher, a built-in module, can roll back any unwanted changes, which means that it will prevent file encryption even for those malware versions that are not yet in antivirus databases.
To find out how this applies to your business follow these tips.
 Ransomware
Ransomware

 Tips
Tips