Kaspersky Lab’s Anti-malware Research Team reported detection of “one of the most dangerous Android banking Trojans ever seen”, called Acecard. Let’s see what makes this malware so dangerous.
Multiple warheads
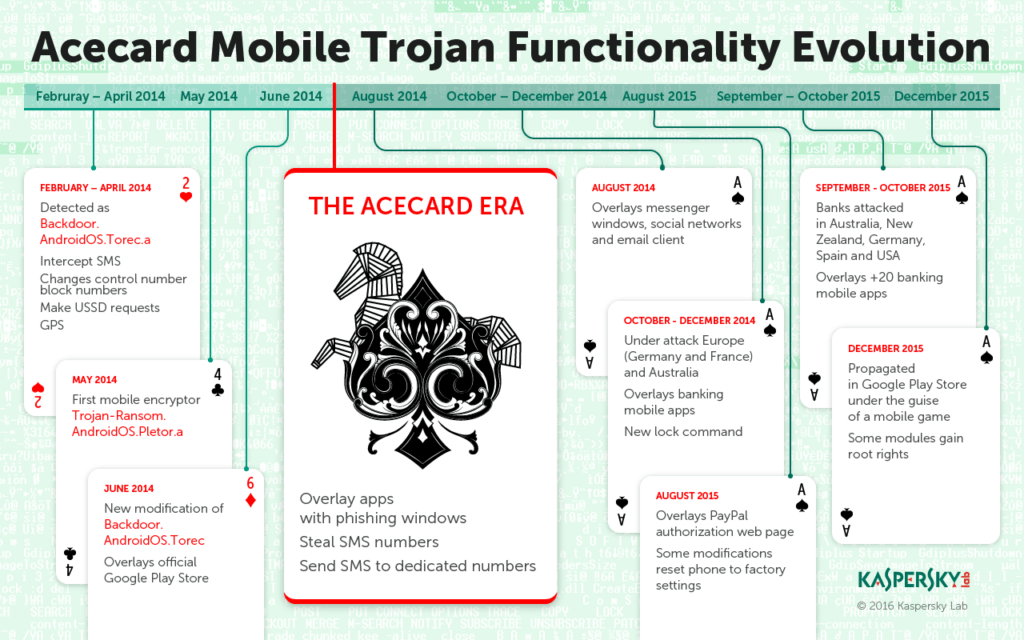
In a nutshell, the primary source of danger Acecard poses is its vast functionality. The Acecard Trojan family can do almost anything malware does today – from stealing a bank’s text and voice messages to overlaying official app windows with false messages that simulate the official login page in an attempt to steal personal information and account details.
The most recent version can attack custom applications of at least 30 banks and online payment services. Besides, it can overlay with phishing windows with such services as WhatsApp, Viber, Instagram, and Skype, along with Facebook, Twitter, Gmail, Google Play and Google Music, and PayPay mobile app.
#Acecard Trojan: many-headed and extremely dangerous. #security
Tweet
Some major regional social networks, such as Russia’s Vkontakte and Odnoklassniki, are also in its reticle, which gives a tip to the origins of the Trojan.
Malware code was studied by Kaspersky lab experts, and they are inclined to think that Acecard was created by the same group of cybercriminals responsible for the first TOR Trojan for Android Backdoor.AndroidOS.Torec.a and the first mobile encryptor/ransomware Trojan-Ransom.AndroidOS.Pletor.a.
The evidence for this is based on similar code lines – names of methods and classes – and the use of the same Command and Controls servers. Acecard was produced by a powerful and experienced group of criminals, most likely Russian-speaking.
Discovery
In the third quarter of 2015, Kaspersky Lab experts detected an unusual increase in the number of mobile banking attacks in Australia. It was soon clear that the culprit is the same malware family.
Acecard was discovered in February 2014, but stayed dormant until the late Spring of 2015. More than 6,000 users were attacked with this Trojan, most of them living in Russia, Australia, Germany, Austria and France.
In the same time period, the Trojan was also in active and continuous development, becoming more and more dangerous.
A Google Play stunt
Somehow criminals managed to slip Acecard downloader into Google’s official app store, under the guise of a game. When the malware is installed from Google Play, the user will only see an Adobe Flash Player icon on the desktop screen and no actual sign of the installed application.
Fortunately, it didn’t last long there.
To learn more about the Acecard Trojan, please read the blog post available at Securelist.com.
Mobile malware tripled
Overall, the volume of mobile malware targeting various kinds of users grew more than three times in 2015, compared to 2014. The most dangerous threats in 2015 were ransomware, malware capable of obtaining unlimited rights on an infected device, and data stealers, including financial malware. These are the main findings of the annual Mobile Virusology report prepared by the Kaspersky Lab Antimalware Research group.
The 2015 mobile threat landscape in numbers:
- 884,774 new malicious programs were detected by Kaspersky Lab, a three-fold increase on 2014 (295, 539).
- The number of new mobile banking Trojans decreased to 7,030 from 16, 586 in 2014.
- 94,344 unique users were attacked by mobile ransomware, a five-fold increase on 2014 (18, 478).
The reason for that is pretty clear: malware attacks on average are successful enough for the criminals to see them as a lucrative business. Hence, attacks grew in numbers, and the malware/ransomware sophistication increased as well.
The number of banking Trojans decreased, but instead they have become much more complex (which is clearly shown by the Acecard story), posing all kinds of threats both to consumers and businesses.
Mobile #malware tripled in 2015. #security
Tweet
Prevention
In order to prevent mobile devices infection (particularly Android) Kaspersky Lab recommends the following:
- Do not download or/and install any applications from Google Play or internal sources if they are untrusted or can be treated as such;
- Do not visit suspicious web pages with specific content and click on suspicious links;
- Install a reliable security solution on mobile devices, such as Kaspersky Internet Security for Android;
- Make sure that antivirus databases are up to date and functioning properly.
Also it is strongly recommended to familiarize yourselves, as well as your company’s staff, with the dominant mobile-related cyberthreats, including phishing, banking Trojans, and how to avoid or counter them.
 Acecard
Acecard
 Tips
Tips