At the end of 2021, Google released its first report on typical threats to cloud users, focusing on the security of Google Cloud Platform. The service provides corporate clients with multiple scenarios for building cloud systems, ranging from simply hosting and running individual applications to deploying high-performance computing.
Reasons for attacking Google Cloud Platform instances
The report focuses on the causes and consequences of attacks on custom GCP instances, analyzing 50 recent successful attacks on custom servers or applications. Of the cases Google analyzed, 48% were the result of a weak password (or no password) for server-based accounts. In 26% of cases, hackers used a vulnerability in the cloud-server software. Server or application misconfiguration enabled 12%, and only 4% were a result of password or access key leaks.
The latter category includes an error not uncommon to developers: uploading authentication data along with source code to a public repository on GitHub or a similar service. According to a report by GitGuardian, up to 5,000 “secrets” (API keys, password/username pairs, certificates) are uploaded to GitHub every day, and 2020 saw 2 million leaks.

Vulnerabilities leaving servers open to hacking, according to Google. Weak or absent passwords enabled most of the attacks. Source.
Google notes that cybercriminals tend not to target specific companies, instead regularly scanning the full range of IP addresses belonging to Google Cloud Platform in search of vulnerable instances. The implication of this automation is clear: If you make an unprotected server accessible from the Internet, it will almost certainly be hacked, and probably soon (in a number of cases, the attack began within 30 minutes of a new instance being raised). The time between hacking and the start of malicious activity is even shorter, with most attacked servers being put into illegal operation within half a minute.
Why attackers go for Google Cloud Platform instances
What do cybercriminals do with cloud resources after hacking them? In the vast majority of cases (86%), a cryptominer (a program that uses the resources of others to generate cryptocurrency) was installed on the server. Most commonly, these are CPU/GPU resources, but the report also mentions the mining of Chia cryptocurrency, which involves the exploitation of free disk space. In another 10% of cases, compromised servers were used for port scanning — to search for new victims. In 8% of cases, an attack on other network resources was made from the server. Rarer types of illegal activities that involve hijacked cloud-platform servers include: hosting malware, prohibited content, or both; carrying out DDoS attacks; and distributing spam.
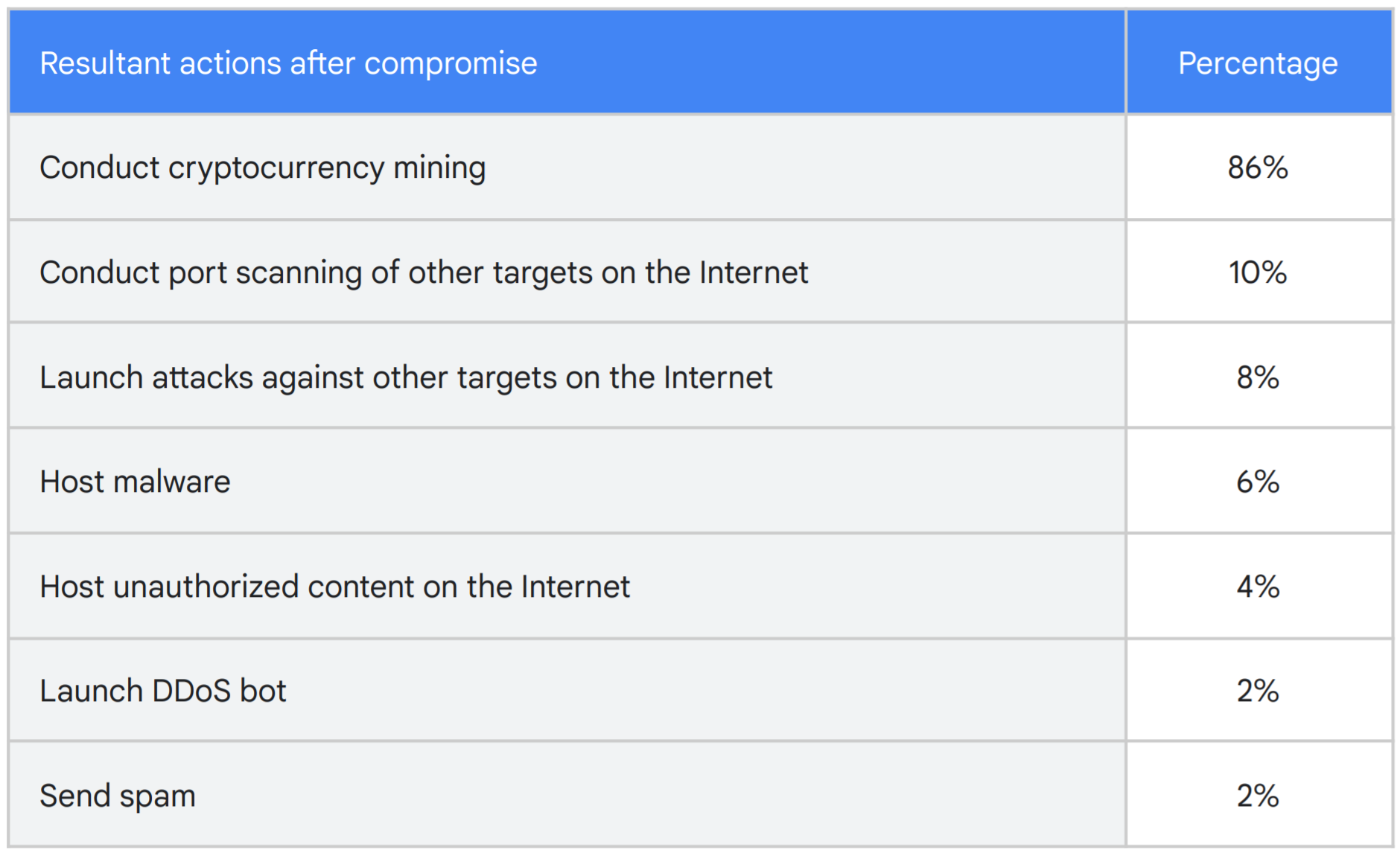
Types of malicious activity on hacked cloud servers. In some cases, several types of illegal operations were carried out simultaneously. Source.
If someone hacks a cloud service and installs a cryptominer, their actions not only harm the client’s reputation and puts access to their own application or website at risk, but victims could face eye-watering service bills as well, even from just a few hours of activity.
Recommendations for securing GCP instances
In most of the cases Google studied, users could have avoided trouble by following minimal security requirements: employing strong passwords and additional authorization factors; ensuring due diligence when uploading source code; and regularly updating installed software to patch known vulnerabilities.
In general, cloud systems require the same protection measures as any other type of infrastructure. They need, at a minimum, regular audits, monitoring of suspicious activity, and isolation of critical data.
But deploying infrastructure in public cloud services involves a few extra recommendations — and not only for organizations using Google Cloud Platform. One of the main ones, as Google notes, is to set automatic conditional alerts to determine when resource consumption exceeds certain thresholds or to spot a rapid increase in costs.
 public cloud
public cloud

 Tips
Tips