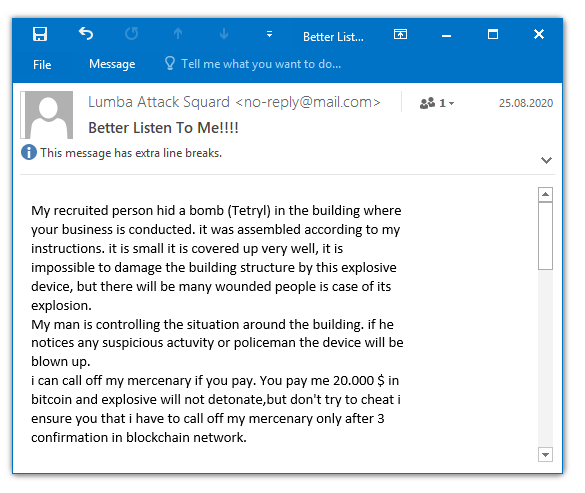
In late August, our mail traps started picking up some unusual blackmail messages. In them, cybercriminals claim to have planted a tetryl-charged bomb somewhere in the recipient’s office and say it will be detonated unless a ransom is paid or if police activity is observed near the building.
In reality, of course, there is no bomb — it’s an empty threat mailed indiscriminately to companies of all sizes. Cybercriminals count on scaring the victim into a knee-jerk response, because with time to think, they will realize that paying ransom solves nothing — if there is a bomb in the building, it’s not going anywhere.
In terms of structure and delivery method, this type of blackmail is the logical continuation of scam mailings threatening to publish users’ private information. The extortionists aren’t choosing specific targets for such threats; they use huge mailing lists and hope that at least some of the recipients will take the threat seriously enough to pay up.
The main difference in the “explosive” version is the increase in the ransom amount. Whereas individuals are asked to cough up the equivalent of $500–1,000 in bitcoin (the maximum we’ve seen was around $5,000), for companies supposedly rigged with explosives the amount rises to roughly $20,000.
The bulk of the scam e-mails are written in German, but we found English versions as well. This batch of attacks appears thus far to be the work of just one entity, but if victims succumb to the threat and transfer money, the method is sure to attract imitators.
Another potentially distinguishing feature of this new wave of extortion e-mails is the potential punishment: Blackmail is a crime in itself, but some countries have separate laws for false bomb threats.
What to do
To avoid becoming a victim of any ransomware scam, we recommend staying vigilant and following a few simple tips:
- Don’t panic — and never pay. Even if the threat were real, yielding to it wouldn’t solve the problem.
- Even if you suspect or know a threat is false, don’t respond; that would only confirm to the attackers that your e-mail address is valid and that the message has been read. And that would only cause the inflow of fraudulent messages and other spam to increase.
- Use reliable security solutions that automatically identify dangerous e-mails and block them before they reach employees’ inboxes.
Our corporate mail security solutions use heuristic algorithms to detect such e-mails. Particularly good at this task are Kaspersky Security for Microsoft Office 365 and Kaspersky Security for Mail Server, which is part of Kaspersky Total Security for Business.
 e-mail
e-mail