
Internet-proof your children with Kaspersky Safe Kids
What if you could be sure that your kids use Internet safely while their mobile phones are protected from fraud, unwanted calls and SMS? All you need for that is Kaspersky Safe Kids!
90 articles

What if you could be sure that your kids use Internet safely while their mobile phones are protected from fraud, unwanted calls and SMS? All you need for that is Kaspersky Safe Kids!

Your legitimate copy of Angry Birds 2 may be infected with malware that steals your private data. How could this happen?

The new trend on IFA 2015 is all about integrity and security. Meet Kaspersky Lab’s observations from the trade show.

Headlines raise alarm: the greatest hack in history finally reached iOS. Is that really so and who are the potential victims?

The number of vulnerable Google devices reached an all-time high since worst Android flaws ever are uncovered. There are already patches available but they may never reach end users.

Cybercriminals know how to benefit from your mobile devices. Be vigilant and follow our recommendations to secure your smartphones and tablets.

Ericsson and Qualcomm are promoting their new technology, LTE-U. Is it any better that LTE-A? And what is this combinations of letters supposed to mean, after all?

A bottle of good scotch in exchange for a day without a smartphone? Would I dare? That’s a piece of cake! That’s what I thought. As it turned out, it’s not that simple nowadays

Which brain mechanisms are in charge of our memory? Kaspersky Lab analyzed why we forget information stored on our devices.

How did you like it the last time you saw your friends? Did you have a nice chat with them? Or were you all only taking pictures of your meals to post them on Instagram and talking to each other on Facebook?

A Trojan malware called Podec uses popular Russian social network VKontakte, and other channels, to infect Android phones. Beware: It can bypass CAPTCHA.

Kaspersky Lab created a mobile app to find a stolen or lost phone, remotely lock it, or delete sensitive data in case of device theft.

Let’s identify the main IT security and protection trends at MWC 2015.

Find out about the most interesting gadgets presented at the Mobile World Congress 2015 in Barcelona

Are you getting enough sleep at night? If not, it might be because your sleep pattern is disrupted due to the display on your PC, TV, tablet, and smartphone.

We have seen a number of cases where a user has deleted our product for Android and ended up with a locked device. Here we discuss why this happens and what can be done about it.
Let’s take a moment to discuss the numerous troubles that our bright, technology-packed future could bring about.

Today, users are readily spending their money on house arrest-style services similar to those used for tracking criminals. They call them fitness trackers.
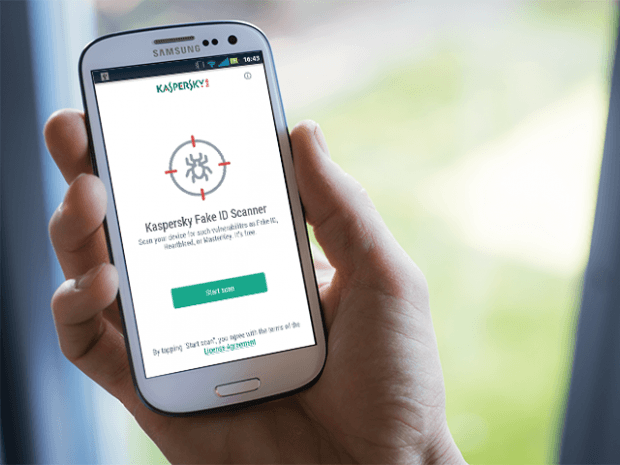
Unpatched flaws in Android make your device vulnerable to “Invisible” infection. You better find out now in order to protect yourself.

Some things we routinely do in the office are dangerous for careers as they pose significant risk to the company’s business. It’s equally relevant for CEO and intern alike, so watch out!

Top Apps to protect you from prying eyes, mischievous kids, thieves, natural disasters, forgetfulness and of course malware.