
Android for cars: Secure connection?
Kaspersky Lab researchers disclose vulnerabilities in connected car apps.
922 articles

Kaspersky Lab researchers disclose vulnerabilities in connected car apps.


An ex-Firefox developer recently said antiviruses are no longer needed. Let’s analyze that claim.

How often do victims succeed in getting back money stolen by online scammers?

We at Kaspersky Lab consider the Adaptive Security Architecture the most efficient model to build up cybersecurity practices for industrial objects

A story of two amateurs who were able to spy on Italian officials for years without getting caught.

It is surprisingly easy to hack airline reservations, obtain banking data and other private information, steal tickets, and rack up air miles.

Contrary to popular belief, viruses for Mac do exist. Other online threats put Mac users at risk as well. Kaspersky Internet Security for Mac can neutralize them all.

As you probably know, Star Wars: Rogue One has hit the theaters to tell the story of the Rebellion who steal the plans of Death Star and facilitate its destruction.

In our previous article on this topic, we looked into the history of memory-only attacks, also taking a glance at attack scenarios and appropriate defensive technologies. Now it is time

Holiday season = more shopping + more targets + more criminals looking to make an easy buck.

What is ransomware? Why do you need to know about it? And how can you protect yourself from it?
Find out if you can avoid traps set by fraudsters for Black Friday sales.
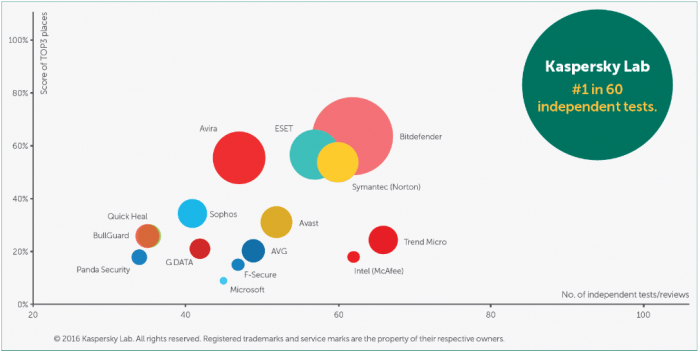
Kaspersky Lab is giving MSPs a chance to get in on the ground floor of an exciting new integration of security and remote monitoring and management tools.

Cybercriminals consider Black Friday and Cyber Monday a great time to steal your money. Here are a few tips on how to stay safe and still have fun.

Analysis shows that the attackers are particularly active during the holiday period.


FAQ about ransomware: types, origins, dangers, and how you can stay safe
Facebook regularly changes its security settings. Take a look: A useful new setting may have appeared since the last time you checked.

It can be tempting to disregard software update notifications. Everything seems to be working fine. Sometimes programs behave oddly or crash after an update. And by the way, you have

Careless behavior online can have devastating personal and financial consequences. Here are seven common shortcuts to avoid.