
Not everybody on the Internet is whom they seem to be
Online dating fraud cost victims millions last year. Be vigilant and protect yourself!
697 articles

Online dating fraud cost victims millions last year. Be vigilant and protect yourself!

When Canada-based adultery site Ashley Madison was hacked, cybercriminals wasted no time in taking advantage of it. Even now, a year later, they continue to blackmail people and hold their data hostage. We look back at what happened then and talk about what’s happening now.

How to protect yourself from ransomware? Are there any cross-platform cryptors? How much time does it take to catch a cybercriminal? Jornt van der Wiel discusses all of that and more

How to keep your money and data safe during the 2016 Olympics: All of the risks you need to know about, in one post.

Kaspersky Lab experts checked industrial control systems for vulnerabilities and found lots of them.

Ranscam deletes your files and then demands ransom to restore them, or it will delete them. Yes, in that order.

Smart MSPs craft security software proposals for SMBs and offer security systems management services that eliminate the need for in-house information security specialists. Not every service provider is good for small companies, but the most successful MSPs are focused on this segment.

You aren’t the only one to catch the PokémonGo craze. So have criminals.
Any USB device can potentially be zombified and turned into a secret agent for cybercrooks. The world needed a shield against this threat, so we rolled up our sleeves and created one.

Once, hackers wrote malware just for the fun of it, but now Trojans are serious business. However, here are five modern, weird malware samples that may be funny and strange, but they are still very dangerous.

Criminals are stealing money from freelancers — by offering them a job.

Apple no longer encrypts the kernel of its iOS operating system. It seems that this is another step towards turning iOS into something similar to Android.

Spanish magazine Red Seguridad recently granted an award to the Kaspersky CyberSafety Management Games training program.

Have you ever received a letter from a Nigerian prince? A Nigerian astronaut? How about Daenerys Targaryen? If so, you know that we are talking about funny Nigerian spam — and this post covers it all!

While we rest, cybercriminals work. Kaspersky Lab discusses the main risks for tourists and travelers on business trips.
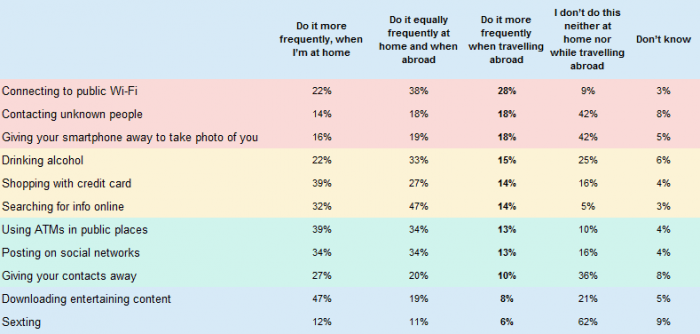
Our survey questioned consumers – 97% of whom had travelled to another country during the past 12 months – about their digital habits abroad. It found that in the world of work and leisure, we are a well-travelled lot, but we tend to leave our digital security at home.

Security should be multilayered, and use of allowlists is appropriate as one of the security levels.

Kaspersky Internet Security and Kaspersky Total Security can help protect your privacy in a variety of ways including not allowing your webcam to serve as a spying device.

It now appears the number of servers bought and sold via xDedic might have been underestimated; it’s likely many more IPs have been compromised by xDedic players.

Let’s talk about new security technologies in Windows 10: Are they enough to make the new operating system totally secure?

This tiny device will help you protect your smartphone from malware and data leakage when charging in public places.