
Sofacy APT turns to the East
Kaspersky Lab publishes an update on Russian-speaking Sofacy APT activity in 2017
108 articles

Kaspersky Lab publishes an update on Russian-speaking Sofacy APT activity in 2017
The story of Kaspersky Lab’s alleged misdeeds is juicy — let’s check out how this fiction is made.

What 2017 will be remembered for, which of our experts’ predictions came true, and what they think about the future

Most modern, enterprise-level companies understand the menace of cyberthreats to business. Some of them have tried to solve cybersecurity problems with the help of system administrators and security software, but

In October 2017, Kaspersky Lab initiated a thorough review of our telemetry logs in relation to alleged 2015 incidents described in the media. These are the preliminary results.

After more than a year of investigation, our experts have a thorough understanding of the Lazarus campaign and advice for protection.

A possible connection between Moonlight Maze, an APT that targeted the Pentagon and NASA in the late 1990s, and Turla, a modern day threat actor.

Kaspersky Lab’s security experts released a detailed report on Operation Ghoul – a targeted campaign aimed primarily at businesses in the Middle East and Europe.

Cyberweapons have to communicate to their creators, propagate within the infrastructure and send data. That’s when an effective and highly flexible algorithm can be capable of spotting them.

ProjectSauron is obviously a costly attack, but the budget is not invested in ‘rocket science’, but rather in the ‘bugfixing’ after the previous APT campaigns.

An Indian-speaking threat actor, Dropping Elephant chooses targets mainly in the Asian region, paying particular attention to Chinese government/diplomatic organizations – and also to foreign embassies and diplomatic offices in China.

It now appears the number of servers bought and sold via xDedic might have been underestimated; it’s likely many more IPs have been compromised by xDedic players.
Securelist just released a new cyberespionage campaign alert, code-named “Operation Daybreak.”
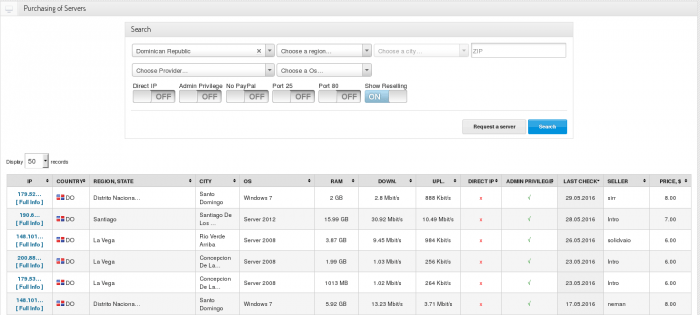
Kaspersky Lab has lately researched an active cybercriminal trading platform xDedic. The main purpose of the xDedic marketplace is to facilitate buying and selling credentials of more than 70,000 hacked servers from all around the world.
A vulnerability affecting all versions of Windows since Windows 2000 through Windows 10 might have been discovered. It’s still uncertain, however.

A new APT group is seen to have been exploiting hotpatching, a now-deprecated feature in Windows operating systems, to carry out their attacks.

Instead of writing their own malicious tools, criminals are increasingly using the off-the-shelf malware, and more and more often – totally legitimate software.

The vast majority of targeted attacks begin with simple steps; spear-phishing with malicious attachments or clickable links, or the infection of employees’ favorite websites (water-holing) to penetrate the security perimeter through the vulnerable browsers or other software. Don’t assume that because these methodologies are well-known, they are any less effective.

Kaspersky Lab launches two new enterprise solutions for preventing the most sophisticated cyberthreats organizations encounter worldwide.